Syntax Verse is a Web3 mining Project. The project was launched on March 17, 2025. This project can earn you a cryptocurrency coin called $SYNTAX. Currently, the Syntax Verse platform has around 50K+ users. The platform has its own apps for Android and IOS devices. You can install the Syntax Verse Android app from the Google Play and App Store. Two interesting features of this platform are the Syntax Verse Daily quiz and the General quiz, which allow users to earn extra $SYNTAX tokens for free by solving Daily and General quiz challenges.
Below is today’s Syntax Verse Daily quiz & General quiz answer.

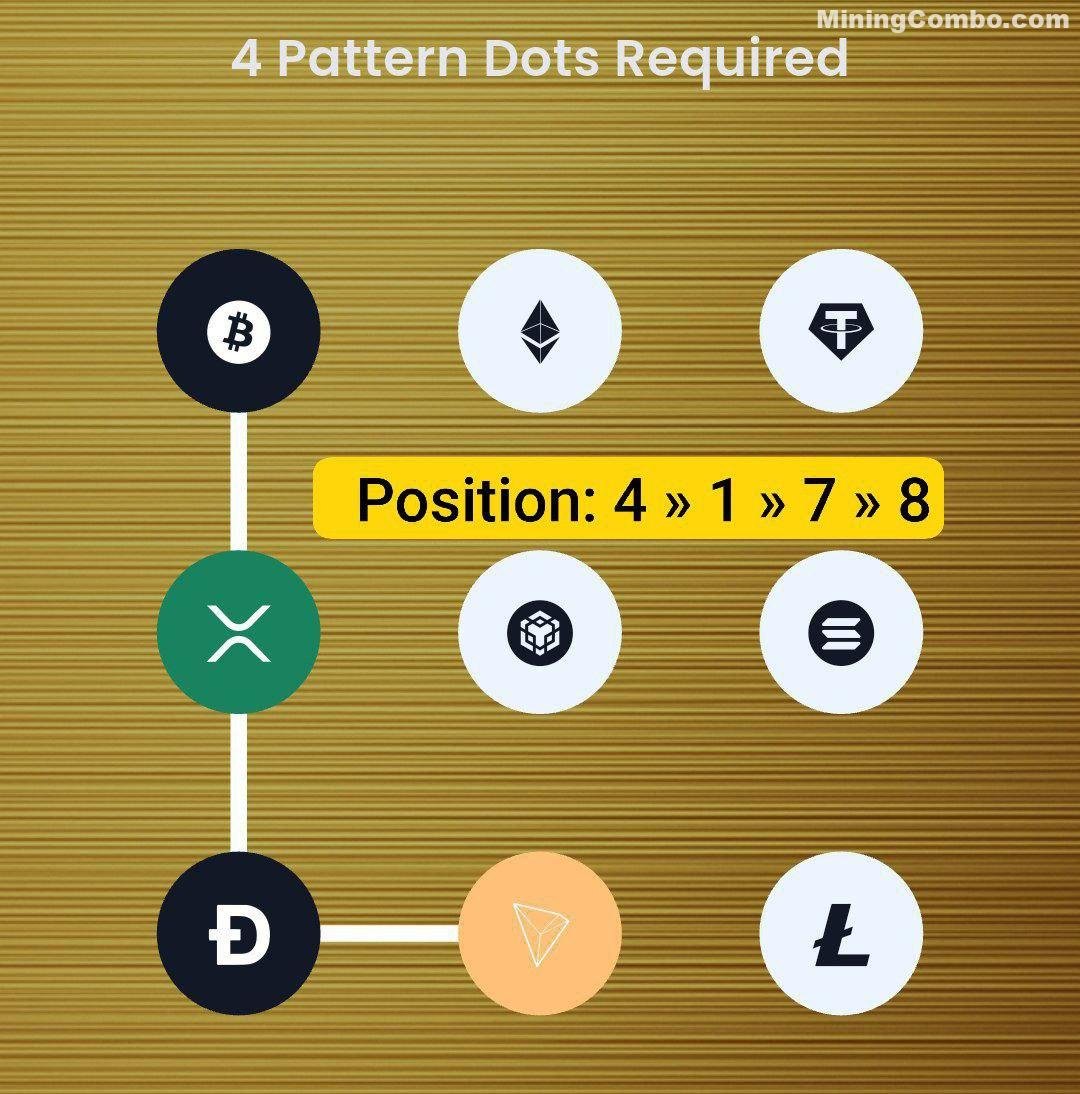
Syntax Verse Daily Vault Pattern Code
Date: 15 November 2025
Syntax Verse Daily General Quiz Answer
Understanding Miner Block Manipulation
Question 1: What does “block manipulation” generally refer to in cryptocurrency mining?
Answer: A) Influencing which transactions go into a block.
Question 2: What allows miners to choose which transactions to include in the next block?
Answer: A) Their computational power.
Question 3: Why might miners reorder transactions in a block?
Answer: C) To maximize their own profit.
Question 4: Which term refers to miners intentionally reordering transactions to gain profit from price differences?
Answer: D) MEV (Miner Extractable Value).
Centralized Exchanges Storage Risks
Question 1: When you store your crypto on a centralized exchange, who technically controls your private keys?
Answer: C) The exchange.
Question 2: What common phrase summarizes the risk of not controlling your own wallet keys?
Answer: B) “Not your keys, not your coins.”
Question 3: Which major exchange collapse in 2022 highlighted the dangers of leaving funds on centralized platforms?
Answer: D) FTX.
Question 4: Why can withdrawals sometimes be halted on centralized exchanges?
Answer: A) Because the exchange may be facing liquidity issues.
PoW vs PoS
Question 1: What is the main reason Proof of Work (PoW) is considered more reliable than Proof of Stake (PoS)?
Answer: B) It has been tested and proven secure for over a decade.
Question 2: In PoW, what do miners compete to solve in order to add a new block?
Answer: A) Cryptographic puzzles.
Question 3: What is one major concern with Proof of Stake systems?
Answer: D) Risk of centralization by wealthy participants.
Question 4: What percentage of mining power would an attacker need to control to compromise a PoW network?
Answer: A) 50%.
Type of Bitcoin Wallet Addresses
Question 1: Which of the following is the original format of Bitcoin wallet addresses?
Answer: B) P2PKH.
Question 2: What prefix do P2SH (Pay-to-Script-Hash) addresses typically start with?
Answer: C) 3.
Question 3: Bech32 addresses are also known as what type of Bitcoin addresses?
Answer: D) SegWit.
Question 4: Which Bitcoin address type is considered most efficient in terms of block space usage?
Answer: C) Bech32.
Question 5: Which Bitcoin address type is best suited for modern wallet compatibility and lowest fees?
Answer: B) Bech32.
Cryptocurrency mining
Question 1: What is the primary purpose of cryptocurrency mining?
Answer: A) Verifying and adding transactions to the blockchain.
Question 2: What kind of algorithm is commonly used in Bitcoin mining?
Answer: A) SHA-256.
Question 3: In proof-of-work mining, what do miners compete to solve?
Answer: C) Mathematical puzzles.
Question 4: What is a “block reward” in mining?
Answer: C) Newly minted coins plus transaction fees.
What Makes a Token Deflationary
Question 1: What does a deflationary cryptocurrency token mean?
Answer: B) Its supply decreases or becomes scarcer over time.
Question 2: What mechanism is most commonly used to make a token deflationary?
Answer: D) Burning tokens.
Question 3: What happens during a token burn?
Answer: A) Tokens are permanently removed from circulation.
Question 4: Which of the following can contribute to a token becoming deflationary over time?
Answer: B) Token burning outpacing new minting.
Public Key in Cryptocurrency
Question 1: What is a public key primarily used for in cryptocurrency?
Answer: C) Receiving cryptocurrency.
Question 2: Which of the following statements best describes a public key?
Answer: B) A cryptographic code derived from a private key.
Question 3: In a cryptocurrency transaction, why is the public key essential?
Answer: A) It provides a destination for the funds.
Question 4: What is the relationship between a public key and a private key?
Answer: D) Private key generates the public key.
Question 5: What happens if someone knows your public key?
Answer: A) They can only send you funds.
Private Key in Cryptocurrency
Question 1: What is a private key in cryptocurrency?
Answer: D) A code that signs transactions and proves ownership.
Question 2: What happens if you lose your private key?
Answer: B) You lose access to your crypto forever.
Question 3: How is a private key usually generated?
Answer: B) Randomly by cryptographic algorithms.
Question 4: What is the relationship between a private key and a public key?
Answer: C) A public key is derived from a private key.
Question 5: Why is it risky to share your private key?
Answer: B) Others can control and spend your crypto.
Flash BTC Transactions
Question 1: What does the term “Flash BTC transaction” generally refer to in cryptocurrency?
Answer: B) A temporary BTC transfer without permanent confirmation.
Question 2: What characteristic is most associated with flash BTC transactions?
Answer: C) Temporarily appearing in the network before disappearing.
Question 3: Why are flash BTC transactions considered risky?
Answer: D) They can disappear before being confirmed.
Question 4: What is the main reason flash BTC transactions occur?
Answer: C) Low transaction fees and mempool manipulation.
Testnets in blockchain
Question 1: What is the main purpose of a testnet in blockchain development?
Answer: D) Testing new features without risking real assets.
Question 2: Which of the following best describes a testnet?
Answer: A) A copy of the blockchain used for experiments.
Question 3: What do testnets typically use instead of real cryptocurrency?
Answer: A) Test tokens with no real-world value.
Question 4: Why are testnets crucial for smart contract deployment?
Answer: B) They allow safe debugging before mainnet launch.
Meme coins on the solana blockchain
Question 1: What is one major reason meme coin creators choose Solana over other blockchains?
Answer: B) Faster transaction speeds.
Question 2: How do Solana’s transaction costs influence meme coin launches?
Answer: A) They make experimentation cheaper.
Question 3: Which feature of Solana helps meme coins handle sudden surges in trading volume?
Answer: B) High throughput.
Question 4: Why does Solana’s developer-friendly ecosystem attract meme coin creators?
Answer: C) It simplifies token deployment.
Seed Phrase In Cryptocurrency
Question 1: What is a seed phrase used for in cryptocurrency wallets?
Answer: C) Recovering wallet access.
Question 2: How many words are typically included in a standard seed phrase?
Answer: B) 12 or 24.
Question 3: If someone knows your seed phrase, they can:
Answer: A) Fully control your wallet.
Question 4: What’s the safest way to store a seed phrase?
Answer: D) Write it down and store it offline.
Choosing the Right Crypto Wallet
Question 1: Which of the following best describes a crypto wallet?
Answer: A) A tool to store, send, and receive cryptocurrencies.
Question 2: What is the main difference between a hot wallet and a cold wallet?
Answer: C) Cold wallets are offline while hot wallets are online.
Question 3: Which type of wallet is generally considered the most secure for long-term storage?
Answer: A) Hardware wallet.
Question 4: What is the primary risk of using an online (hot) wallet?
Answer: B) Hackers targeting internet-connected devices.
Question 5: Why is a seed phrase important when choosing a crypto wallet?
Answer: D) It acts as your wallet’s backup key.
Al Crypto Security
Question 1: What is one of the main uses of AI in cryptocurrency security?
Answer: D) Detecting suspicious transactions in real time
Question 2: How can AI help prevent phishing attacks targeting crypto wallets?
Answer: C) By analyzing behavioral patterns in communication
Question 3: What advantage does AI bring to smart contract auditing?
Answer: B) It detects vulnerabilities faster than manual review
Question 4: Which AI approach is commonly used to detect abnormal on-chain activity?
Answer: A) Anomaly detection models
Bitcoin vs Ethereum
Question 1: What is the primary purpose of Bitcoin in the cryptocurrency ecosystem?
Answer: B) Acting as a peer-to-peer digital currency.
Question 2: Which network introduced the concept of smart contracts?
Answer: C) Ethereum.
Question 3: What is the maximum supply limit of Bitcoin?
Answer: B) 21 million.
Question 4: Which of the two cryptocurrencies was launched first?
Answer: C) Bitcoin.
Layer 2 Solutions in Blockchain
Question 1: What is the main purpose of Layer 2 solutions in blockchain?
Answer: ✅ D) To improve network scalability
Question 2: Which of the following is an example of a Layer 2 solution for Ethereum?
Answer: ✅ B) Polygon
Question 3: What technology does Optimistic Rollups rely on for fraud prevention?
Answer: ✅ C) Fraud proofs
Question 4: Which of these is NOT a Layer 2 scaling solution?
Answer: ✅ A) Sharding
Origin of NFT
Question 1: What does NFT stand for in the crypto world?
Answer: B) Non-Fungible Token.
Question 2: Which year is widely credited as the beginning of NFTs?
Answer: C) 2014.
Question 3: Which project is considered the first true NFT?
Answer: C) Quantum.
Question 4: What is the main purpose NFTs were originally intended for?
Answer: B) Digital ownership and provenance.
Crypto Market Fluctuation
Question 1: What does “crypto market volatility” refer to?
Answer: D) The rapid change in cryptocurrency prices.
Question 2: Which factor often contributes most to short-term crypto price fluctuations?
Answer: C) Market sentiment and news.
Question 3: When a crypto asset experiences a “pump and dump,” what happens?
Answer: C) Price spikes quickly and then crashes.
Question 4: What usually happens when Bitcoin’s price drops significantly?
Answer: A) Most altcoins follow the downtrend.
Question 5: What is the main reason stablecoins exist in volatile crypto markets?
Answer: B) To offer a safe haven during market swings.
Arbitrum
Question 1: What is Arbitrum primarily known as in the blockchain ecosystem?
Answer: A) A Layer 2 scaling solution.
Question 2: Arbitrum is built to scale which blockchain?
Answer: C) Ethereum.
Question 3: Which technology does Arbitrum use to achieve scalability?
Answer: B) Optimistic Rollups.
Question 4: What is the main purpose of Arbitrum?
Answer: B) Reducing transaction costs and increasing speed.
Relay Nodes
Question 1: What is the main purpose of a relay node in a blockchain network?
Answer: C) Facilitating communication between nodes.
Question 2: In the Bitcoin Lightning Network, what role does a relay node play?
Answer: D) Routing payments between channels.
Question 3: Relay nodes in Proof-of-Stake networks like Polkadot are mainly responsible for:
Answer: C) Bridging parachains.
Question 4: How does a relay node differ from a validator node?
Answer: B) Relay nodes forward data, validators participate in consensus.
Bounty Programs in Cryptocurrency
Question 1: What is a cryptocurrency bounty program primarily designed for?
Answer: A) To reward users for completing specific tasks.
Question 2: Which of the following is a common task in a crypto bounty program?
Answer: B) Promoting the project on social media.
Question 3: What is the main purpose of a bug bounty in crypto projects?
Answer: D) Find and report vulnerabilities in code.
Question 4: Which type of bounty helps projects with language and localization?
Answer: D) Translation bounty.
Inter-Blockchain Communication (IBC) Protocol
Question 1: What is the primary purpose of the Inter-Blockchain Communication (IBC) protocol?
Answer: B) To enable interoperability between different blockchains.
Question 2: Which blockchain ecosystem is most closely associated with the IBC protocol?
Answer: D) Cosmos.
Question 3: What type of architecture does IBC follow for cross-chain communication?
Answer: A) Hub-and-Spoke.
Question 4: What is the primary role of a “relayer” in the IBC protocol?
Answer: C) Transfers packets of data between blockchains.
Question 5: What would happen if an IBC relayer goes offline?
Answer: B) Packets stop moving until another relayer picks them up.
Cosmos Blockchain
Question 1: What is the main purpose of the Cosmos network in blockchain?
Answer: D) To enable cross-chain interoperability
Question 2: Which consensus mechanism does Cosmos use in its Tendermint core?
Answer: D) Tendermint BFT
Question 3: What is the primary token of the Cosmos ecosystem?
Answer: A) ATOM
Question 4: What role does the Cosmos Hub play in the network?
Answer: A) It acts as a centralized database
Algorand Blockchain
Question 1: What consensus mechanism does Algorand use?
Answer: C) Pure Proof-of-Stake.
Question 2: Who is the founder of Algorand?
Answer: A) Silvio Micali.
Question 3: In which year was the Algorand mainnet launched?
Answer: C) 2019.
Question 4: What is the native token of the Algorand network?
Answer: B) ALGO.
Fan Token
Question 1: What is the primary purpose of a fan token in the cryptocurrency ecosystem?
Answer: A) To allow fans to interact and influence team decisions
Question 2: Which platform is widely known for launching fan tokens for major sports teams?
Answer: B) Socios.com
Question 3: Fan tokens are typically built on which blockchain standard?
Answer: D) ERC-20
Question 4: What is a unique feature of fan tokens compared to regular cryptocurrencies?
Answer: A) They are used for NFT staking
Token Deflation
Question 1: What does “token deflation” generally refer to in crypto?
Answer: B) Decreasing token supply over time.
Question 2: Which mechanism is commonly used to create token deflation?
Answer: C) Token burning.
Question 3: Why do projects introduce token deflation mechanisms?
Answer: A) To increase scarcity and potentially value.
Question 4: Which of these cryptocurrencies introduced a major deflationary mechanism through EIP-1559?
Answer: B) Ethereum.
Liquid Staking
Question 1: What is liquid staking in cryptocurrency?
Answer: A) Staking tokens while retaining liquidity through derivatives.
Question 2: Which of the following is a primary benefit of liquid staking?
Answer: B) Allows tokens to be traded while still earning staking rewards.
Question 3: What do liquid staking platforms typically issue to users?
Answer: ) Derivative tokens representing staked assets.
Question 4: Which protocol is well-known for enabling liquid staking on Ethereum?
Answer: D) Lido.
Question 5: What is the typical reason users prefer liquid staking over traditional staking?
Answer: C) Ability to unstake immediately without waiting period.
ENS
Question 1: What does ENS stand for in cryptocurrency?
Answer: B) Ethereum Name Service
Question 2: What is the main purpose of ENS?
Answer: C) Converting Ethereum addresses into readable names
Question 3: ENS domains typically end with which extension?
Answer: A) .eth
Question 4: Which blockchain does ENS primarily operate on?
Answer: D) Ethereum.
Layer 0 Protocols
Question 1: What is the main function of a Layer 0 protocol in blockchain architecture?
Answer: A) Providing the base infrastructure for multiple Layer 1 blockchains.
Question 2: Which of the following is a well-known Layer 0 protocol?
Answer: C) Polkadot.
Question 3: Cosmos is a Layer 0 protocol that uses what communication standard?
Answer: B) IBC (Inter-Blockchain Communication).
Question 4: Which of these is a key benefit of Layer 0 protocols?
Answer: C) Enhanced interoperability.
Oracles in Crypto
Question 01: What is a crypto oracle?
Answer: D) A bridge between blockchains and external data.
Question 02: Why do blockchains need oracles?
Answer: C) To access off-chain data.
Question 03: Which of the following is a well-known oracle network?
Answer: B) Chainlink.
Question 04: What kind of data can oracles provide?
Answer: C) Any real-world or off-chain data.
What Makes Nodes Decentralized
Question 1: What is a node in a blockchain network?
Answer: A) A server that stores and shares blockchain data.
Question 2: Why are blockchain networks considered decentralized?
Answer: C) They operate through multiple independent nodes.
Question 3: What role do nodes play in blockchain decentralization?
Answer: B) They validate and propagate data across the network.
Question 4: Which of the following increases decentralization in a blockchain?
Answer: A) More nodes operated by different people globally.
Gas War
Question 1: What is a gas war in the context of crypto?
Answer: B) A bidding competition for transaction priority.
Question 2: Gas wars usually happen during…
Answer: C) High-demand NFT minting events.
Question 3: What does ‘gas’ refer to in Ethereum?
Answer: B) Transaction processing fee.
Question 4: Why do users increase gas fees during a gas war?
Answer: D) To get their transactions processed faster.
Why TVL Isn’t Always What It Seems
Question 1: What does TVL stand for in DeFi?
Answer: B) Total Value Locked.
Question 2: Why might TVL not reflect the real activity in a DeFi protocol?
Answer: C) TVL can be inflated by token prices.
Question 3: What is one common way TVL can appear artificially high?
Answer: A) By double-counting assets across protocols.
Question 4: Which of these is NOT a good reason to question a high TVL?
Answer: D) Protocol has high trading volume.
Stablecoins – Collateralized vs. Algorithmic
Question 1: What is the main purpose of a stablecoin in the crypto ecosystem?
Answer: A) To maintain a stable value against fiat currency.
Question 2: Which of the following is an example of a fiat-collateralized stablecoin?
Answer: C) USDT (Tether).
Question 3: What backs a crypto-collateralized stablecoin?
Answer: D) Other cryptocurrencies.
Question 4: Which of the following best describes algorithmic stablecoins?
Answer: A) They adjust supply and demand automatically through code.
Token Swapping
Question 01: What does “token swapping” usually refer to in crypto?
Answer: C) Exchanging one cryptocurrency token for another.
Question 02: Which platform is most commonly associated with token swapping on Ethereum?
Answer: B) Uniswap.
Question 03: What type of exchange is typically used for token swaps without an intermediary?
Answer: D) Decentralized Exchange (DEX).
Question 04: What is typically required to execute a token swap on a DEX?
Answer: B) A crypto wallet connected to the platform.
Cross-Chain Bridges
Question 01: What is the primary purpose of a cross-chain bridge in blockchain technology?
Answer: A) To allow assets and data to move between different blockchains.
Question 02: Which of the following is a well-known cross-chain bridge?
Answer: B)Rainbow Bridge.
Question 03: What type of token is commonly moved using cross-chain bridges?
Answer: A) Wrapped tokens.
Question 04: What is a major security risk associated with cross-chain bridges?
Answer: C) Vulnerability to exploits and hacks.
State Channel
Question 01: What is a state channel in blockchain?
Answer: D) An off-chain method for conducting transactions.
Question 02: Why are state channels used in blockchain networks?
Answer: A) To improve scalability and speed.
Question 3: Which network is known for using state channels?
Answer: C) Lightning Network.
Question 4: What’s one major benefit of using state channels?
Answer: B) Fast and cheap transactions.
On-chain governance
Question 01: What is the main goal of on-chain governance?
Answer: C) To allow protocol changes through blockchain-based voting.
Question 02: In on-chain governance, who typically votes on proposed changes?
Answer: B) Token holders or validators.
Question 03: Which of the following is a common voting mechanism in on-chain governance?
Answer: A) Proof-of-Stake Voting.
Question 04: What happens if a proposal is accepted in on-chain governance?
Answer: B) Changes are implemented automatically or semi-automatically.
Sidechain
Question 01: What is a sidechain in blockchain technology?
Answer: B) A separate blockchain connected to a main chain.
Question 02: What is the main benefit of using a sidechain?
Answer: C) Scalability and faster transactions.
Question 03: Sidechains are often used to:
Answer: D) Experiment with new features and reduce congestion.
Question 04: What links a sidechain to a main chain?
Answer: B) Cross-chain bridges.
Question 05: Can sidechains have their own consensus mechanisms?
Answer: C) Yes, they can use independent consensus.
Flashbots
Question 01: What are Flashbots primarily designed to combat?
Answer: B) Miner Extractable Value (MEV) issues.
Question 02: What is MEV short for in the context of Flashbots?
Answer: C) Maximum Extractable Value.
Question 03: Flashbots primarily operate on which blockchain network?
Answer: D) Ethereum.
Question 04: What tool does Flashbots use to allow private transaction submission?
Answer: A) Flashbots Protect.
OlympusDAO
Question 01: What is the native token of OlympusDAO?
Answer: B) OHM.
Question 02: What type of economic model does OlympusDAO use?
Answer: D) Elastic Supply
Question 03: OlympusDAO aims to create a:
Answer: A) Reserve currency.
Question 04: OlympusDAO’s treasury backs each OHM token with:
Answer: C) A basket of assets.
DeFi 2.0
Question 1: What is DeFi 2.0 primarily focused on improving compared to DeFi 1.0?
Answer: A) Liquidity sustainability and protocol-owned liquidity.
Question 2: Which concept is central to DeFi 2.0 protocols like OlympusDAO?
Answer: B) Protocol-owned liquidity (POL).
Question 3: What does POL (Protocol-Owned Liquidity) reduce reliance on?
Answer: C) Temporary liquidity incentives.
Question 4: Which is a commonly mentioned benefit of DeFi 2.0?
Answer: D) Sustainable and self-owned liquidity.
Monero
Question 1: What is the primary focus of Monero as a cryptocurrency?
Answer: B) Privacy and anonymity.
Question 2: What algorithm does Monero use for mining?
Answer: C) RandomX.
Question 3: What is a key privacy feature that Monero uses?
Answer: A) Ring signatures.
Question 4: Unlike Bitcoin, Monero hides:
Answer: B) The sender, receiver, and amount of transactions.
Question 5: What is the ticker symbol for Monero?
Answer: D) XMR.
subDAOs
Question 1: What does the term “SubDAO” stand for?
Answer: C) Sub-Decentralized Autonomous Organization.
Question 2: What is a SubDAO primarily used for within a DAO structure?
Answer: D) Delegating responsibilities and governance.
Question 3: Which of the following best describes a SubDAO’s relationship to the main DAO?
Answer: A) It handles specific tasks or sectors within the main DAO.
Question 4: What is one of the benefits of using SubDAOs?
Answer: C) Better scalability and specialization.
Question 5: What is one risk of using SubDAOs?
Answer: D) Governance fragmentation or coordination issues.
Securities laws
Question 1: What is a security in financial terms?
Answer: D) An investment contract or tradable financial asset.
Question 2: Why are securities laws important in crypto?
Answer: C) To protect investors and prevent fraud.
Question 3: Which U.S. organization enforces securities laws?
Answer: B) SEC.
Question 4: What does the Howey Test determine?
Answer: A) If something is a security.
Social engineering in crypto
Question 1: What does “social engineering” mean in the context of crypto?
Answer: B) Manipulating people to give up confidential info.
Question 2: Which of the following is an example of social engineering?
Answer: A) Sending a phishing email posing as a crypto exchange.
Question 3: What’s a common goal of social engineering attacks in crypto?
Answer: B) To access a user’s private key or wallet.
Question 4: What is a “phishing” attack in crypto?
Answer: C) Tricking users to enter private data on fake sites.
Front-running in DeFi
Question 1: What does front-running in DeFi typically involve?
Answer: B) Placing a transaction in front of someone else’s for profit.
Question 2: Which platform characteristic enables front-running in DeFi?
Answer: B) Public mempools.
Question 3: Front-running is considered a type of which of the following?
Answer: C) MEV (Miner Extractable Value.
Question 4: Which network condition increases the chance of front-running?
Answer: C) High network congestion.
Reentrancy Attacks
Question 1: What is a reentrancy attack in smart contracts?
Answer: C) An exploit where a function is called repeatedly before previous executions complete.
Question 2: Which blockchain platform is most associated with reentrancy attacks?
Answer: A) Ethereum.
Question 3: What famous 2016 incident involved a reentrancy attack?
Answer: B) DAO hack.
Question 4: Which function behavior is typically exploited in a reentrancy attack?
Answer: D) External calls before state updates.
Multisig Wallet
Question 1: What does “multisig” stand for in crypto wallets?
Answer: B) Multiple signatories.
Question 2: What is the main benefit of using a multisig wallet?
Answer: C) Extra security.
Question 3: In a 2-of-3 multisig wallet, how many signatures are needed to approve a transaction?
Answer: B) 2.
Question 4: Which of these wallets is known to support multisig functionality?
Answer: A) Electrum.
Gas Fees in Layer 2s
Question 1: What is the main purpose of Ethereum Layer 2 solutions?
Answer: C) Reduce gas fees and increase transaction speed.
Question 2: Which of the following is a Layer 2 scaling solution?
Answer: C) Arbitrum.
Question 3: How do Layer 2s reduce Ethereum gas fees?
Answer: D) By bundling multiple transactions into one.
Question 4: What is a potential drawback of using Layer 2 solutions?
Answer: C) Increased complexity or security risks.
Smart Contract Security
Question 1: What is one of the first steps you should take when checking if a smart contract is safe?
Answer: A) Review the contract code or audit report.
Question 2: What does a verified smart contract on Etherscan typically mean?
Answer: B) The code matches what’s deployed.
Question 3: Which of the following is a common sign of a malicious smart contract?
Answer: C) Hidden or obfuscated functions.
Question 4: Why is community feedback helpful when judging a smart contract?
Answer: A) It can expose past fraud or issues.
MICA
Question 1: What does MiCA stand for in crypto regulation?
Answer: B) Markets in Crypto-Assets.
Question 2: Which region introduced the MiCA regulation?
Answer: C) European Union.
Question 3: Which of the following is a primary goal of MiCA?
Answer: A) Provide a legal framework for crypto-assets.
Question 4: True or False: MiCA bans the use of Bitcoin in the EU.
Answer: B) False.
Question 5: Which type of crypto projects are excluded from MiCA?
Answer: D) All of the above.
Wallet Privacy
Question 1: What is the main purpose of a cryptocurrency wallet?
Answer: D) To store and manage private/public keys
Question 2: Are most blockchain transactions publicly visible?
Answer: B) Yes, on most public blockchains.
Question 3: What is an “alt wallet”?
Answer: C) An alternative wallet address you also use.
Question 4: Which method is NOT helpful for improving wallet privacy?
Answer: B) Reusing addresses.
Finality Blockchain
Question 1: What does ‘finality’ mean in a blockchain context?
Answer: B) The point where a transaction cannot be reversed.
Question 2: Which of these best describes probabilistic finality?
Answer: C) Finality that increases with more blocks mined.
Question 3: Which blockchain uses instant (deterministic) finality?
Answer: D) Tendermint-based chains (e.g., Cosmos).
Question 4: Finality is important in blockchain because it:
Answer: C) Prevents double spending.
Liquidity in Crypto
Question 1: What does ‘liquidity’ mean in cryptocurrency markets?
Answer: B) How easily an asset can be converted into cash or another coin.
Question 2: High liquidity means:
Answer: C) You can buy/sell quickly with minimal price impact.
Question 3: Which of the following contributes to high liquidity?
Answer: D) High trading volume and many market participants.
Question 4: Which of these assets is typically more liquid?
Answer: A) Bitcoin on Binance.
How to identify a fake crypto exchange
Question 1: What is a common red flag of a fake crypto exchange website?
Answer: A) Spelling errors and bad grammar.
Question 2: Which URL feature should you always verify before using a crypto exchange?
Answer: C) HTTPS and domain spelling.
Question 3: What’s a risky sign during account registration?
Answer: C) Requesting private keys or seed phrases.
Question: Fake exchanges often promise:
Answer: B) Guaranteed high returns.
Zero-Knowledge Proofs
Question 1: What does “zero-knowledge” refer to in Zero-Knowledge Proofs?
Answer: C) Verifying without revealing information.
Question 2: Which of the following is a key characteristic of Zero-Knowledge Proofs?|
Answer: C) Privacy-preserving verification.
Question 3: In the context of ZKPs, what is a “prover”?
Answer: B) A person who proves they know something.
Question 4: ZK-SNARK stands for:
Answer: A) Zero-Knowledge Succinct Non-Interactive Argument of Knowledge.
Flash loans in crypto
Question 1: What is a flash loan in crypto?
Answer: A) A loan that must be paid back within the same transaction.
Question 2: Which DeFi platform is most known for introducing flash loans?
Answer: B) Aave.
Question 3: What is required to take out a flash loan?
Answer: A) Nothing, just code and logic.
Question 4: What happens if a flash loan is not repaid in the same transaction?
Answer: C) The transaction fails completely.
Forks in Blockchain (Soft vs. Hard Forks)
Question 1: What is a blockchain fork?
Answer: C) A split in the blockchain protocol or chain.
Question 2: Which of the following best defines a hard fork?
Answer: A) A change that makes previously valid blocks invalid.
Question 3: What is a soft fork?
Answer: B) A backward-compatible upgrade.
Question 4: In a hard fork, what must users typically do to stay on the main chain?
Answer: A) Upgrade to new protocol software.
Question 5: What happens if miners disagree during a hard fork?
Answer: D) A split occurs, creating separate chains.
Private Key Management Best Practices
Question 01: What is a private key used for in cryptocurrency?
Answer: A) Confirming transactions and accessing funds.
Question 02: Which of the following is the most secure way to store your private key?
Answer: C) Hardware wallet.
Question 03: What is a seed phrase?
Answer: B) A recovery phrase for your private key.
Question 04: Which of these actions is a bad practice in private key management?
Answer: D) Sharing your private key with a friend.
The Future of Web3 Applications
Question 1: What is a key goal of Web3 applications?
Answer: B) User data ownership.
Question 2: Which technology is most critical to the functioning of Web3?
Answer: B) Blockchain.
Question 3: Which of these best describes a Web3 wallet?
Answer: C) A browser extension for managing digital identity and tokens.
Question 4: Which Web3 application area is growing fast in gaming?
Answer: A) Blockchain-based play-to-earn games.
What Is a Wallet Signature & Why It Matters
Question 1: What is a wallet signature in crypto?
Answer: D) A unique cryptographic proof you control a wallet.
Question 2: What type of key is used to generate a wallet signature?
Answer: B) Private key.
Question 3: Why are wallet signatures important in Web3 apps?
Answer: A) They prove ownership without revealing your password.
Question 4: Which of the following can a wallet signature verify?
Answer: C) That you own a specific wallet address.
What is a retroactive airdrop in crypto?
Question 1: What is a retroactive airdrop in crypto?
Answer: A) A token distribution based on past user activity.
Question 2: Which of these is a common reason projects do retroactive airdrops?
Answer: C) To reward early adopters and testers.
Question 3: Which protocol famously gave a retroactive airdrop in 2020 to early users?
Answer: B) Uniswap
Question 4: To be eligible for a retroactive airdrop, what is typically required?
Answer: A) Past interaction with the protocol.
Interchain Messaging
Question 1: What does “interchain messaging” allow in the blockchain world?
Answer: B) Communication between different blockchains.
Question 2: Which of the following best describes a cross-chain bridge?
Answer: C) A tool for transferring data or assets across blockchains.
Question 3: What is a common use case of interchain messaging?
Answer: C) Asset transfers between blockchains.
Question 4: Which protocol is known for enabling interchain communication in the Cosmos ecosystem?
Answer: C) IBC (Inter-Blockchain Communication).
The Use of Blockchain in Healthcare Data Privacy
Question 1: What is one major benefit of using blockchain for healthcare data storage?
Answer: A) Improved data privacy and security.
Question 2: In blockchain-based healthcare systems, who typically controls access to medical records?
Answer: C) The patient.
Question 3: Which key blockchain feature helps protect healthcare records from tampering?
Answer: B) Immutability.
Question 4: Which of the following is NOT an advantage of blockchain in healthcare?
Answer: D) Transparent data sharing.
Question 5: How can blockchain enhance patient consent processes?
Answer: C) Through transparent, trackable permissions.
How Blockchain Enables Cross-Border Payments
Question 1: What is one of the main advantages of using blockchain for cross-border payments?
Answer: A) Real-time settlement
Smart Contract Risks.
Question 2: Which feature of blockchain helps remove the need for intermediaries in cross-border transactions?
Answer: B) Smart contracts.
Question 3: What type of ledger does blockchain use?
Answer: A) Distributed ledger.
Question 4: What makes blockchain-based international payments more accessible?
Answer: C) Internet access and digital wallets.
How DAG-Based Cryptocurrencies Work
Question 1: What does DAG stand for in blockchain technology?
Answer: A) Directed Acyclic Graph.
Question 2: Which cryptocurrency is well-known for using a DAG structure?
Answer: C) IOTA.
Question 3: In a DAG-based cryptocurrency, how are transactions verified?
Answer: A) Each new transaction approves previous ones.
Question 4: Which of the following is a benefit of using DAG over traditional blockchains?
Answer: C) Scalability for microtransactions.
The Role of Soulbound Tokens in Web3
Question 1: What is a Soulbound Token (SBT)?
Answer: B) A non-transferable token tied to an identity.
Question 2: What makes Soulbound Tokens different from traditional NFTs?
Answer: C) They cannot be transferred or sold.
Question 3: What kind of information could be represented using SBTs?
Answer: A) Educational credentials and achievements.
Question 4: Who proposed the idea of Soulbound Tokens?
Answer: C) Vitalik Buterin.
Smart Contract Risks
Question 1: What is a common risk of smart contracts if the code is poorly written?
Answer: C) Smart contract hacks.
Question 2: Why can smart contracts be risky once deployed to the blockchain?
Answer: D) Their code becomes unchangeable.
Question 3: What kind of attack tricks a smart contract into calling back into itself repeatedly?
Answer: B) Reentrancy.
Question 4: What happens if a smart contract lacks proper input validation?
Answer: A) Users can exploit its functions.
Blockchain Security
Question 1: What is the primary purpose of blockchain security?
Answer: C) To protect data from tampering or unauthorized access.
Question 2: What is a 51% attack in blockchain?
Answer: A) When a single entity controls over 51% of the network’s mining power.
Question 3: What is a private key in blockchain security?
Answer: B) A secret code used to access your crypto.
Question 4: Which of the following helps protect blockchains from tampering?
Answer: D) Cryptographic hashing and consensus mechanisms.
How SIM Swaps Can Lead to Crypto Theft
Question 1: What is the main goal of a SIM swap attack?
Answer: C) To gain control of a user’s phone number.
Question 2: Why is access to your phone number dangerous in crypto security?
Answer: B) It lets attackers receive two-factor authentication (2FA) codes.
Question 3: Which type of account is most often compromised after a SIM swap?
Answer: D) Cryptocurrency wallets and exchanges.
Question 4: Which form of 2FA is safer than using SMS for crypto accounts?
Answer: A) Authenticator apps like Google Authenticator.
Multi-Party Computation (MPC) in Crypto Security
Question 1: What is the main purpose of Multi-Party Computation (MPC) in crypto security?
Answer: B) To allow multiple parties to compute a result without revealing private inputs.
Question 2: In MPC, each party holds a piece of the data. What is this concept called?
Answer: C) Secret Sharing
Question 3: Which of the following is a common real-world use case of MPC in crypto?
Answer: A) Secure key management for crypto wallets.
Question 4: In MPC-based wallets, how is the private key handled?
Answer: B) Broken into shares distributed among parties.
Token burning explained
Question 1: What is token burning in the context of cryptocurrency?
Answer: A) Deleting tokens from circulation permanently.
Question 2: What is the main purpose of burning tokens?
Answer: C) Reduce supply to potentially increase value.
Question 3: What address are tokens usually sent to when burned?
Answer: B) Zero address (0x000…000).
Question 4: Which of the following is a common reason projects burn tokens?
Answer: A) To increase scarcity and investor interest.
Crypto Culture & Slangs
Question 1: What is a “whale” in crypto slang?
Answer: C) A person who holds large amounts of crypto.
Question 2: What does “HODL” stand for in crypto slang?
Answer: A) Hold On for Dear Life.
Question 3: If someone is said to be “rekt” in crypto, what happened?
Answer: B) They lost a lot of money.
Question 4: What does “FOMO” mean in crypto investing?
Answer: D) Fear of Missing Out.
Question 5: What is “FUD” short for in the crypto world?
Answer: C) Fear, Uncertainty, Doubt.
Proof of Stake
Question 1: What does “staking” typically involve in a Proof of Stake blockchain?
Answer: B) Locking up coins to validate transactions.
Question 2: Which of the following blockchains uses Proof of Stake (PoS)?
Answer: A) Ethereum (post-Merge).
Question 3: In PoS, validators are chosen based on:
Answer: C) The size and duration of their stake.
Question: What is one major benefit of Proof of Stake over Proof of Work?
Answer: C) It’s more energy-efficient.
Real World Assets
Question 1: What does the term “Real World Assets” (RWAs) refer to in the context of blockchain?
Answer: B) Physical assets represented on-chain.
Question 2: Which of the following is not typically considered a Real World Asset?
Answer: D) Bitcoin.
Question 3: What is the primary benefit of tokenizing Real World Assets on a blockchain?
Answer: C) Increases liquidity and accessibility.
Question 4: Which type of blockchain token is often used to represent Real World Assets?
Answer: D) Security token.
How Bitcoin Addresses Are Generated
Question 1: What is the first step in generating a Bitcoin address?
Answer: D) Generating a private key.
Question 2: Bitcoin private key is typically represented as:
Answer: B) A 256-bit number.
Question 3: Which algorithm is used to create a public key from a private key in Bitcoin?
Answer: C) ECDSA (secp256k1).
Question 4: What is added to the beginning of a Bitcoin address before Base58 encoding?
Answer: B) A version byte.
How Blockchain Works.
Question 1: What is a blockchain?
Answer: B) A decentralized and distributed ledger.
Question 2: What is the main purpose of blockchain technology?
Answer: B) To enable secure and transparent transactions.
Question 3: How are transactions verified in a blockchain network?
Answer: B) By network participants using consensus mechanisms.
Question 4: What ensures the security of blockchain data?
Answer: B) The use of cryptographic hash functions.
Question 5: What is the role of miners in a Proof of Work (PoW) blockchain?
Answer: A) They solve complex mathematical problems to validate transactions.
Question 6: What does a blockchain hash represent?
Answer: D) A unique identifier for a block’s data.
Question 7: What is an immutable ledger?
Answer: C) A blockchain where past transactions cannot be altered.
Question 8: What happens when a block is added to the blockchain?
Answer: D) It is linked to the previous block with a hash.
Question 9: What is a “fork” in blockchain?
Answer: A) A split in the blockchain, creating two separate chains.
Question 10: What is a private blockchain?
Answer: C) A blockchain controlled by a single entity with restricted access.
Bitcoin Innovation History!
Question 1: Which year was Bitcoin created?
Answer: B) 2009.
Question 2: What is the smallest unit of Bitcoin called?
Answer: B) Satoshi.
Question 3: Which of the following cryptocurrencies is known as the first smart contract platform?
Answer: C) Ethereum.
Question 4: What is the maximum supply of Bitcoin that can ever exist?
Answer: B) 21 million BTC.
Ethereum (ETH)
Question 1: Who is the founder of Ethereum?
Answer: B) Vitalik Buterin.
Question 2: What is the native cryptocurrency of the Ethereum blockchain?
Answer: A) ETH.
Question 3: What type of consensus mechanism does Ethereum use after the Merge?
Answer: C) Proof of Stake (PoS).
Question 4: What is the name of Ethereum’s upgrade that transitioned it from Proof of Work to Proof of Stake?
Answer: B) The Merge.
Question 5: What is the purpose of “gas” in Ethereum?
Answer: C) It is a fee required to process transactions and smart contracts.
Question 6: Which Ethereum standard is commonly used to create fungible tokens?
Answer: A) ERC-20.
Question 7: What is the Ethereum Virtual Machine (EVM)?
Answer: C) A computation engine that executes smart contracts on Ethereum.
Crypto Mining
Question 1: What is crypto mining?
Answer: C) Verifying and adding transactions to the blockchain.
Question 2: What is a mining rig?
Answer: A) A specialized computer for mining.
Question 3: What do miners compete to solve in Proof of Work?
Answer: B) Hash puzzles.
Question 4: What is the reward for mining Bitcoin?
Answer: D) New BTC coins.
Question 5: What is a mining pool?
Answer: B) A group of miners sharing resources.
Question 6: Which coin cannot be mined?
Answer: A) Ethereum.
Question 7: What does “block time” refer to?
Answer: B) Time needed to mine a block.
Smart Contracts
Question 1: What is a smart contract?
Answer: B) A blockchain-based program that executes automatically when conditions are met.
Question 2: Which blockchain introduced smart contracts?
Answer: C) Ethereum.
Question 3: Which of the following is NOT a characteristic of smart contracts?
Answer: A) Can be reversed after deployment.
Question 4: Where are smart contracts stored?
Answer: D) On blockchain networks.
Question 5: Can smart contracts be modified after deployment?
Answer: B) No, they are immutable unless designed with upgradability.
Binance chain (BSC)
Question 1: What is the native cryptocurrency of Binance Smart Chain (BSC)?
Answer: B) BNB.
Question 2: What consensus mechanism does Binance Smart Chain (BSC) use?
Answer: D) Proof of Staked Authority (PoSA).
Question 3: Which token is primarily used for fungible tokens on Binance Smart Chain?
Answer: B) BEP-20.
Question 4: What is the main purpose of Binance Chain (now BNB Chain)?
Answer: A) To enable high-speed and low-cost decentralized applications (DApps).
Question 5: What is PancakeSwap, and how is it related to Binance Smart Chain?
Answer: A) A decentralized exchange (DEX) built on BSC.
Decentralized Finance (DeFi)
Question 1: What is DeFi?
Answer: B) A decentralized financial ecosystem.
Question 2: What powers most DeFi applications?
Answer: D) Smart contracts.
Question 3: Which blockchain is most commonly used for DeFi?
Answer: C) Ethereum.
Question 4: What is impermanent loss?
Answer: A) Price volatility risk in liquidity pools.
Question 5: What is staking?
Answer: A) Locking tokens to earn rewards.
Question 6: What does a decentralized exchange (DEX) do?
Answer: B) Allows peer-to-peer crypto trading.
Stablecoins
Question 1: What is a stablecoin?
Answer: B) A digital asset pegged to a stable value.
Question 2: Which asset is commonly used to back stablecoins?
Answer: C) Commodities.
Question 3: What can cause a stablecoin to lose its peg?
Answer: A) Lack of reserves or panic selling.
Question 4: What is the main advantage of stablecoins?
Answer: B) Stable value for transactions.
Question 5: What makes a stablecoin different from Bitcoin?
Answer: D) Pegged value.
Question 6: What happens when a stablecoin de-pegs?
Answer: B) It loses its stable value.
Cold Storage
Question 1: What is cold storage in crypto?
Answer: B) Offline crypto storage.
Question 2: Which is a type of cold storage?
Answer: A) Paper wallet.
Question 3: What is the main benefit of cold storage?
Answer: C) Higher security.
Question 4: Why is cold storage safer than hot wallets?
Answer: B) Offline, less hackable.
Question 5: What is an air-gapped wallet?
Answer: A) Internet-free cold storage.
Question 6: What is a disadvantage of cold storage?
Answer: D) Slower access.
DAOs in Crypto
Question 1: What does DAO stand for?
Answer: B) Decentralized Autonomous Organization.
Question 2: How are decisions made in a DAO?
Answer: A) Smart contracts and community voting.
Question 3: What technology powers DAOs?
Answer: C) Blockchain and smart contracts.
Question 4: What is the primary benefit of DAOs?
Answer: D) Full decentralization and transparency.
Question 5: How do members participate in a DAO?
Answer: C) Holding governance tokens.
Question 6: Why are DAOs important in Web3?
Answer: B) They promote community-driven governance.
Question 7: What is a major challenge of DAOs?
Answer: D) Legal uncertainty in regulations.
Crypto Taxes & Regulations
Question 1: How are cryptocurrencies classified for tax purposes in most countries?
Answer: C) As property.
Question 2: What is a taxable event in crypto?
Answer: D) Selling crypto for a profit.
Question 3: What tax applies when crypto is exchanged for another crypto?
Answer: B) Capital gains tax.
Question 4: What happens if you don’t report crypto earnings on your taxes?
Answer: C) Tax penalties.
Question 5: What is the main goal of crypto regulations?
Answer: B) Ensure fair markets and prevent fraud.
Question 6: What does KYC stand for in crypto exchanges?
Answer: B) Know Your Customer.
Crypto Wallets & Security
Question 1: What is a crypto wallet used for?
Answer: A) Storing and managing private keys.
Question 2: Which wallet type is considered the safest?
Answer: C) Hardware wallet.
Question 3: What is the main risk of using a custodial wallet?
Answer: D) No control over private keys.
Question 4: What does a seed phrase do?
Answer: B) Recovers a lost wallet.
Question 5: How can you protect your crypto wallet?
Answer: C) Enable two-factor authentication.
Question 6: What happens if you lose your private key?
Answer: D) Your funds are permanently lost.
Question 7: What is phishing in crypto security?
Answer: C) Tricking users into revealing private keys.
NFT
Question 1: What does NFT stand for?
Answer: C) Non-Fungible Token.
Question 2: What makes an NFT unique?
Answer: B) It cannot be duplicated.
Question 3: Where are NFTs typically stored?
Answer: C) On a blockchain.
Question 4: What is a smart contract?
Answer: A) A digital agreement on blockchain.
Question 5: What is the purpose of an NFT marketplace?
Answer: B) To buy, sell, and trade NFTs.
Question 6: What gives NFTs their value?
Answer: B) Supply, demand, and rarity.
Web3
Question 1: What is Web3?
Answer: B) A decentralized version of the web.
Question 2: Which technology powers Web3?
Answer: A) Blockchain.
Question 3: What is the key feature of Web3?
Answer: B) User ownership of data.
Question 4: Which cryptocurrency is most associated with Web3?
Answer: C) Ethereum.
Question 5: What does “decentralization” mean in Web3?
Answer: A) Distributed power across users.
Question 6: What is the main difference between Web2 and Web3?
Answer: C) Web3 is decentralized.
Question 7: Web3 only works with crypto
Answer: A) A Web3 search engine.
DEFI
Question 1: What does DeFi stand for in the cryptocurrency space?
Answer: A) Decentralized Finance.
Question 2: Which blockchain is most commonly used for DeFi applications?
Answer: C) Ethereum.
Question 3: What is “yield farming” in DeFi?
Answer: B) Earning rewards by staking or providing liquidity to DeFi platforms.
Question 4: Which of the following is a popular decentralized exchange (DEX)?
Answer: C) Uniswap
Question 5: What is the main purpose of a liquidity pool in DeFi?
Answer: B) To provide liquidity for trading pairs on decentralized exchanges.
Question 6: What is an Automated Market Maker (AMM) in DeFi?
Answer: B) A mechanism that replaces traditional order books in DEXs by using liquidity pools.
Question 7: Which DeFi protocol is best known for decentralized lending and borrowing?
Answer: B) Aave.
Question 8: What is impermanent loss in DeFi?
Answer: B) The temporary loss of value when providing liquidity due to price fluctuations of tokens.
SyntaxVerse; Explore the crypto world
Question 1: What primary benefit does SyntaxVerse offer to users?
Answer: B) Interactive Web3 education and rewards.
Question 2: How can users earn rewards on SyntaxVerse?
Answer: B) By completing blockchain-related tasks and quizzes.
Question 3: Which feature of SyntaxVerse allows users to test their knowledge and win crypto prizes?
Answer: C) Web3 Quizzes.
Question 4: What is the purpose of the referral system in SyntaxVerse?
Answer: C) To invite friends and boost earnings.
Question 5: What educational content does SyntaxVerse focus on?
Answer: B) Web3, blockchain, and crypto concepts.
Crypto Trading
Question 1: What is crypto trading?
Answer: C) Buying and selling crypto for profit.
Question 2: What does “HODL” mean in crypto trading?
Answer: B) Long-term holding.
Question 3: What is the purpose of a stop-loss order?
Answer: D) Prevent excessive losses.
Question 4: What is the main advantage of using a crypto exchange?
Answer: B) Access to multiple trading pairs.
Question 5: What is Bitcoin dominance?
Answer: A) The percentage of Bitcoin’s market cap compared to total crypto market.
Question 6: What is a decentralized exchange (DEX)?
Answer: B) A peer-to-peer trading platform.
Digital Signatures
Question 1: What is a digital signature used for?
Answer: C) Verifying authenticity and integrity.
Question 2: What is required to verify a digital signature?
Answer: B) Public key.
Question 3: Why are hash functions used in digital signatures?
Answer: C) To generate a fixed-size fingerprint of data.
Question 4: What makes digital signatures secure?
Answer: A) Cryptographic algorithms.
Automated Market Makers (AMMS)
Question 1: What do AMMs replace in crypto trading?
Answer: B) Order books.
Question 2: Which platform popularized AMMs?
Answer: A) Uniswap.
Question 3: What do AMMs use to set prices?
Answer: B) Algorithms.
Question 4: Who provides liquidity to AMMs?
Answer: D) Users.
Types of Cryptocurrencies
Question 1: What is the first cryptocurrency ever created?
Answer: C) Bitcoin.
Question 2: Which type of cryptocurrency is designed for fast transactions?
Answer: B) Litecoin.
Question 3: What is the main purpose of stablecoins?
Answer: A) Maintain a fixed value.
Question 4: Which of these is a stablecoin?
Answer: A) Tether USD (USDT).
Question 5: What makes privacy coins unique?
Answer: D) Hide transaction details.
Question 6: Which blockchain specializes in NFTs?
Answer: A) Flow.
Question 7: Which cryptocurrency focuses on fast cross-border payments?
Answer: C) Ripple (XRP).
Question 8: What is a governance token?
Answer: B) Allows voting on project decisions.
Consensus Mechanisms in Crypto
Question 1: What is the purpose of a consensus mechanism?
Answer: B) Verify transactions.
Question 2: Which consensus model does Bitcoin use?
Answer: A) Proof of Work.
Question 3: What is required in Proof of Work (PoW)?
Answer: C) Solving complex puzzles.
Question 4: How does Proof of Stake (PoS) select validators?
Answer: A) Based on the number of tokens staked.
Question 5: What is a weakness of Proof of Work?
Answer: D) High energy use.
Yield Farming
Question 1: What is yield farming?
Answer: A) Earning rewards by providing liquidity.
Question 2: What do users provide in yield farming?
Answer: D) Liquidity to DeFi pools.
Question 3: Where is yield farming commonly used?
Answer: B) Decentralized finance (DeFi).
Question 4: What do liquidity providers receive?
Answer: D) Interest or governance tokens.
Question 5: What is impermanent loss?
Answer: A) Loss due to price changes in liquidity pools.
Question 6: What is APY in yield farming?
Answer: C) Annual percentage yield.
Question 7: What can impact yield farming rewards?
Answer: B) Market volatility.
Question 8: What is a farming pool?
Answer: C) A smart contract holding deposited funds.
Importance of Liquidity Mining in DeFi Growth
Question 1: What is liquidity mining?
Answer: C) Providing liquidity to earn rewards.
Question 2: Which of these is typically rewarded in liquidity mining?
Answer: B) Governance tokens.
Question 3: Where does liquidity mining usually take place?
Answer: A) Decentralized exchanges (DEXs).
Question: What risk can liquidity providers face?
Answer: B) Impermanent loss.
The Role of Full Nodes in Bitcoin
Question 1: What is a full node in the Bitcoin network?
Answer: C) A computer that stores and validates the entire blockchain.
Question 2: Why are full nodes important in Bitcoin?
Answer: B) They enforce the rules of the Bitcoin protocol.
Question 3: Which of the following is NOT done by a full node?
Answer: C) Mining new blocks.
Question 4: How does a full node contribute to decentralization?
Answer: B) By spreading out control of network rules.
Question 5: Can a full node operate without mining?
Answer: B) Yes.
How Crypto Differs from Traditional Digital Payments
Question 1: Traditional digital payments like PayPal are usually controlled by:
Answer: B) Centralized institutions.
Question 2: Bitcoin transactions are recorded on a:
Answer: C) Public blockchain.
Question 3: Which is true about crypto payments?
Answer: C) They are peer-to-peer.
Question 4: Which of the following is not a feature of traditional digital payment systems?
Answer: A) Decentralization.
Cybersecurity Awareness
Question 1: What is a “phishing attack” in the cryptocurrency space?
Answer: B) A scam where attackers trick users into revealing private keys or passwords.
Question 2: Which of the following is the safest way to store cryptocurrencies?
Answer: A) Using a paper wallet or hardware wallet.
Question 3: What does “2FA” stand for in crypto security?
Answer: D) Two-Factor Authentication.
Question 4: What is a “rug pull” in cryptocurrency?
Answer: C) A scam where developers abandon a project after taking investors’ funds.
Question 5: What is the purpose of a “cold wallet” in cryptocurrency?
Answer: A) To store cryptocurrencies offline for better security.
Question 6: Which of these is a common security threat in decentralized finance (DeFi)?
Answer: B) Smart contract exploits.
Bitcoin ATMS
Question 1: What is a Bitcoin ATM?
Answer: B) A machine to buy and sell Bitcoin.
Question 2: What do you need to use a Bitcoin ATM?
Answer: A) A crypto wallet.
Question 3: What does a Bitcoin ATM issue after a transaction?
Answer: B) A paper receipt.
Question 4: What is a key disadvantage of Bitcoin ATMs?
Answer: A) High transaction fees.
How Cryptojacking Infects Computers for Mining
Question 1: What is cryptojacking?
Answer: B) Unauthorized use of a device to mine cryptocurrency.
Question 2: Which of the following is a common way cryptojacking malware enters a device?
Answer: C) Phishing emails.
Question 3: What does cryptojacking primarily consume on a victim’s computer?
Answer: B) CPU and GPU resources.
Question 4: One sign your computer might be cryptojacked is:
Answer: D) Overheating and slow performance.
Question 5: What’s a good way to prevent browser-based cryptojacking?
Answer: B) Installing browser extensions that block mining scripts.
Bitcoin’s Role in the Silk Road Marketplace
Question 1: What was the Silk Road in the context of Bitcoin’s early history?
Answer: B) A dark web marketplace.
Question 2: Which key feature of Bitcoin made it appealing for use on Silk Road?
Answer: D) Pseudonymous transactions.
Question 3: What platform was the Silk Road accessible through?
Answer: C) Tor browser.
Question 4: In which year was the Silk Road shut down by the FBI?
Answer: B) 2013.
The Use of Multi-Party Computation (MPC) in Crypto Security
Question 1: What is Multi-Party Computation (MPC) primarily used for in crypto?
Answer: A) Securely managing private keys.
Question 2: In an MPC system, who has access to the full private key?
Answer: C) No single party.
Question 3: How does MPC enhance crypto wallet security?
Answer: B) By splitting the private key across multiple devices.
Question 4: What does MPC stand for?
Answer: D) Multi-Party Computation.
How SIM Swaps Can Lead to Crypto Theft
Question 1: What is a SIM swap attack?
Answer: C) Taking over someone’s phone number to access sensitive accounts.
Question 2: Why do attackers perform SIM swap attacks on crypto users?
Answer: A) To bypass two-factor authentication and access crypto wallet.
Question 3: What is usually the first step in a SIM swap scam?
Answer: B) Contacting the victim’s mobile provider with fake ID.
Question 4: How can SIM swap lead directly to crypto theft?
Answer: D) It allows access to verification codes for exchanges.
Question 5: What can you do to protect against SIM swap attacks?
Answer: A) Use an authenticator app or hardware 2FA.
Permissioned & Permissionless Blockchains
Question 1: What is the main feature of a permissionless blockchain?
Answer: B) Anyone can participate in the network.
Question 2: Which of the following is an example of a permissionless blockchain?
Answer: C) Bitcoin.
Question 3: Permissioned blockchains are generally used by:
Answer: D) Private organizations.
Question 4: Which statement best describes permissioned blockchains?
Answer: A) They have restricted access and governance.
Question 5: A key downside of permissionless blockchains is:
Answer: C) Slower transaction speeds.
Crypto Bonds
Question 1: What is a crypto bond?
Answer: A) A blockchain-based version of a traditional bond.
Question 2: Which of the following best describes the main purpose of crypto bonds?
Answer: B) To raise funds by offering returns over time.
Question 3: Which blockchain has been notably used to issue crypto bonds?
Answer: A) Ethereum.
Question 4: What risk is associated with crypto bonds?
Answer: C) Lack of regulatory clarity.
Lending & Borrowing in DeFi
Question 1: What is one of the key reasons people use DeFi lending platforms?
Answer: D) To earn passive income on idle assets.
Question 2: In DeFi, what is typically required before borrowing funds?
Answer: C) Collateral deposit.
Question 3: What does LTV stand for in DeFi lending?
Answer: B) Loan-To-Value.
Question 4: Which of the following is a popular DeFi lending platform?
Answer: C) Compound.
NFT
Question 1: What does NFT stand for?
Answer: C) Non-Fungible Token.
Question 2: What makes an NFT unique?
Answer: B) It cannot be duplicated.
Question 3: Where are NFTs typically stored?
Answer: C) On a blockchain.
Question 4: What is a smart contract?
Answer: A) A digital agreement on blockchain.
Question 5: What is the purpose of an NFT marketplace?
Answer: B) To buy, sell, and trade NFTs
Question 6: What gives NFTs their value?
Answer: B) Supply, demand, and rarity.
How to Choose a Crypto Exchange
Question 1: What is a crypto exchange used for?
Answer: B) Buying, selling, and trading cryptocurrency.
Question 2: Which of the following is most important when choosing a crypto exchange?
Answer: C) Security and reputation.
Question 3: What does KYC stand for in crypto exchanges?
Answer: D) Know Your Customer.
Question 4: If you want full control of your funds, you should choose a:
Answer: A) Decentralized exchange (DEX).
Risks of Smart Contract Vulnerabilities
Question 1: What is a smart contract in the context of blockchain?
Answer: C) Self-executing code with rules written on blockchain.
Question 2: Which programming language is most commonly used for Ethereum smart contracts?
Answer: A) Solidity.
Question 3: What is a reentrancy attack?
Answer: C) An attacker calling back into a contract before the first function finishes.
Question 4: Which famous hack involved a reentrancy vulnerability?
Answer: A) The DAO Hack.
Dark Pools in Crypto Trading?
Question 1: What is a dark pool in crypto trading?
Answer: A) A private exchange for large trades.
Question 2: Why do traders use dark pools?
Answer: C) To maintain privacy and reduce market impact.
Question 3: Which of these is a potential risk of dark pools?
Answer: B) Lack of market transparency.
Question 4: What’s one benefit of using a dark pool?
Answer: A) Lower slippage on large trades.
How Web3 Gaming Differs from Traditional Gaming
Question 1: What is a key feature that differentiates Web3 gaming from traditional gaming?
Answer: A) Ownership of in-game assets.
Question 2: Which technology enables true ownership of digital items in Web3 games?
Answer: B) Smart Contracts.
Question 3: In traditional gaming, where are in-game assets usually stored?
Answer: C) Centralized servers.
Question 4: Which of these platforms is most likely used in Web3 gaming?
Answer: C) Ethereum.
The Future of Al-Powered Crypto Trading
Question 1: What does AI stand for in crypto trading?
Answer: B) Artificial Intelligence.
Question 2: One key benefit of using AI in crypto trading is:
Answer: C) Emotionless decision-making.
Question 3: What does a crypto trading bot typically do?
Answer: D) Buys/sells crypto based on set rules.
Question 4: What’s a major ethical concern with AI crypto trading?
Answer: C) It may give unfair advantage to a few.
How Play-to-Earn Games Use NFTs
Question 1: What does “Play-to-Earn” (P2E) mean in crypto gaming?
Answer: C) Playing games to earn cryptocurrency or digital assets.
Question 2: In Play-to-Earn games, what role do NFTs usually play?
Answer: B) As characters, skins, or items players can own.
Question 3: Which of these is a real example of a Play-to-Earn game?
Answer: A) Axie Infinity.
Question 4: What technology makes NFTs work in Play-to-Earn games?
Answer: B) Blockchain.
The Role of Al & Machine Learning in Web3
Question 1: What is one key role of AI in Web3 applications?
Answer: D) Automating smart contract audits.
Question 2: How does machine learning improve decentralized finance (DeFi)?
Answer: A) By predicting market trends.
Question 3: In Web3, AI can help detect which of the following?
Answer: C) Fraudulent activities or scams.
Question 4: AI models in Web3 can reduce bias in:
Answer: B) Content moderation and governance decisions.
Cross-Chain Interoperability
Question 1: What is cross-chain interoperability?
Answer: A) Communication between different blockchains.
Question 2: What enables blockchains to interact?
Answer: C) Bridges and interoperability protocols.
Question 3: What is a blockchain bridge?
Answer: B) A tool for transferring assets between chains.
Question 4: What does a wrapped token represent?
Answer: C) A token pegged to an asset on another blockchain.
Question 5: Why is cross-chain interoperability important?
Answer: A) It allows seamless asset transfers between networks.
Question 6: What is an example of a cross-chain protocol?
Answer: B) Polkadot.
Understanding Gas Fees
Question 1: What are gas fees in crypto?
Answer: C) Transaction costs on a blockchain.
Question 2: Which blockchain is known for high gas fees?
Answer: B) Ethereum.
Question 3: What factors determine gas fees?
Answer: A) Network congestion and transaction complexity.
Question 4: Who receives gas fees in a Proof-of-Work network?
Answer: D) Miners.
Question 5: What happens if a gas fee is too low?
Answer: C) Transaction may fail or be delayed.
Question 6: What can help reduce gas fees?
Answer: A) Using Layer 2 solutions.
Question 7: What happens if a transaction runs out of gas?
Answer: B) It fails but fees are still deducted.
Tokenomics
Question 1: What does Tokenomics refer to?
Answer: A) Study of token usage and distribution.
Question 2: What is a token supply limit?
Answer: C) Maximum number of tokens that will ever exist.
Question 3: What happens in a token burn?
Answer: C) Tokens are removed from circulation.
Question 4: What is the purpose of staking in Tokenomics?
Answer: A) Securing the network and earning rewards.
Question 5: What is a token vesting schedule?
Answer: B) Gradual release of locked tokens.
Question 6: Which factor affects a token’s price the most?
Answer: D) Supply and demand.
Question 7: How are governance tokens used?
Answer: A) Voting on project decisions.
Question 8: What is a token airdrop?
Answer: B) Free distribution of tokens.
Why Private Keys Should Never Be Shared
Question 1: What is a private key in cryptocurrency?
Answer: B) A code that allows you to access and control your crypto wallet.
Question 2: What happens if someone else gets your private key?
Answer: A) They can send crypto on your behalf.
Question 3: Which of the following should you do with your private key?
Answer: C) Store it securely and keep it secret.
Question 4: Which storage method is safest for private keys?
Answer: A) Writing it down on paper and hiding it.
Question 5: What kind of wallet gives you full control over your private key?
Answer: C) Non-custodial wallet.
Hash Functions in Blockchain
Question 1: What is the primary role of a hash function in blockchain technology?
Answer: B) Ensure data integrity.
Question 2: Which of the following best describes a cryptographic hash function?
Answer: A) Deterministic and one-way.
Question 3: Which hash function is used in Bitcoin?
Answer: C) SHA-256.
Question 4: What makes hash functions important for digital signatures?
Answer: B) Collision.
Note: We are researching the Syntax Verse Web3 airdrop project. We will update this page with more details about the Syntax Verse Web3 mining Project. Thanks.

























































